使用云盘CDS
概述
容器引擎 CCE 支持通过创建 PV/PVC,并为工作负载挂载数据卷方式使用百度智能云磁盘CDS。本文将介绍如何在集群中动态和静态挂载云磁盘。
使用限制
- 集群 Kubernetes 版本需大于或等于 1.16。
- 挂载 CDS 的 Pod 只能在支持挂载云磁盘的节点上启动。
- 每个节点挂载的 CDS 数量由 CCE CSI CDS Plugin 组件配置参数及云服务器自身同时决定,更多信息请见创建服务器实例。
- 当前云盘只支持按量付费的方式进行挂载,不支持包年包月的付费方式创建。
前提条件
- 集群已安装块存储组件,更多信息请见 CCE CSI CDS Plugin 说明。
操作步骤
通过 PV/PVC 方式使用 CDS,具体分为两种方式:
| 方式 | 说明 | 注意事项 |
|---|---|---|
| 静态挂载 | 需要用户提前在百度智能云中创建好 CDS(操作方法参考 CDS 文档),然后通过 CDS 的 volume id 在集群中创建 PV 和 PVC 资源。 |
|
| 动态挂载 | 用户在集群中声明 PVC 时,自动创建出按量付费 CDS 磁盘并且动态关联至 PV。 |
|
动态挂载块存储
方式一:通过 kubectl 命令行操作
1. 创建存储类 StorageClass
- 集群管理员可使用 StorageClass 为集群定义不同的存储类型。您可通过 StorageClass 配合 PVC 动态创建需要的存储资源。
- 本文介绍通过 Kubectl 方式创建云盘 CDS 类型的 StorageClass,自定义块存储使用所需的模板。
1apiVersion: storage.k8s.io/v1
2kind: StorageClass
3metadata:
4 name: hp1 #StorageClass名称
5provisioner: csi-cdsplugin
6allowVolumeExpansion: true
7volumeBindingMode: WaitForFirstConsumer
8parameters:
9 paymentTiming: "Postpaid" #付费方式,Postpaid 表示按量付费,当前只支持按量付费
10 storageType: "hp1" #磁盘类型,支持cloud_hp1, hp1, hdd
11 recycle: "on" #云磁盘的删除回收策略,支持 on、off(on 表示删除时将云磁盘放入回收站,off 表示删除时云磁盘不放入回收站),仅当 reclaimPolicy 为 Delete 生效,默认值为 on
12reclaimPolicy: Delete #云磁盘的删除策略,支持 Delete、Retain(Delete 表示删除 PVC 时,PV 和 云磁盘会一起删除,删除云磁盘默认放入回收站;Retain 表示删除 PVC 时,PV和云磁盘不会被删除,需要您手动删除),默认为 Delete说明:
- storageType 用于设置动态创建的 CDS 盘的类型,支持:cloud_hp1 (通用型 SSD)、hp1 (高性能云磁盘)、hdd(通用型 HDD),更多信息参见 创建CDS云盘。
- 如果集群中存在使用动态方式挂载 CDS 的 Pod,且对应 StorageClass 中 reclaimPolicy 设置为 Delete,这部分 CDS 在集群删除集群时默认会保留,如果需要一同删除请在删除集群前手动停止相关 Pod 并删除对应 PVC。
2. 创建持久卷声明 PVC
注意 storageClassName 需要指定为上述部署 storageClass 时填写的 storageClass 名称。
1kind: PersistentVolumeClaim
2apiVersion: v1
3metadata:
4 name: csi-pvc-cds
5spec:
6 accessModes:
7 - ReadWriteOnce
8 storageClassName: hp1
9 resources:
10 requests:
11 storage: 5Gi # 指定PVC存储空间大小说明: 不同的磁盘类型,存储大小不同,如 hp1 : 5~32765GB,cloud_hp1 : 50~32765GB,hdd : 5~32765GB
3. 检查 PVC 状态为 Bound
1$ kubectl get pvc csi-pvc-cds
2NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
3csi-pvc-cds Bound pvc-1ab36e4d1d2711e9 50Gi RWO hp1 4s说明:
如果指定了 volumeBindingMode 为
WaitForFirstConsumer,则 PVC 此时处于 Pending 状态,会等待第一个挂载该 PVC 的 Pod 被创建后才进入 PV 创建和绑定流程。
4. 在 Pod 中挂载 PVC
Pod 和 PVC 需要在同一个 namespace 下。
1apiVersion: v1
2kind: Pod
3metadata:
4 name: test-pvc-pod
5 labels:
6 app: test-pvc-pod
7spec:
8 containers:
9 - name: test-pvc-pod
10 image: nginx
11 volumeMounts:
12 - name: cds-pvc
13 mountPath: "/cds-volume"
14 volumes:
15 - name: cds-pvc
16 persistentVolumeClaim:
17 claimName: csi-pvc-cdsPod 创建后,可以读写容器内的 /cds-volume 路径来访问相应的 cds 存储上的内容。
方式二:通过控制台操作
- 登陆 CCE 控制台,点击集群名称进入集群详情页。
- 创建存储类 StorageClass。
a. 在左侧导航栏中选择存储配置 > 存储类,进入存储类列表页面。
b. 在存储类列表上方点击新建存储类。在文件模版中自定义相关配置。storageType 用于设置动态创建的 CDS 盘的类型,支持:cloud_hp1 (通用型 SSD)、hp1 (高性能云磁盘)、hdd(通用型 HDD)。
b. 点击确定,将为您创建存储类。
- 创建持久卷声明 PVC。
a. 在左侧导航栏选择存储配置 > 持久卷声明,进入持久卷声明列表。
b. 点击持久卷声明列表上方新建持久卷声明按钮,选择表单创建或 Yaml 创建。
c. 若选择表单创建则需填写相关参数,其中三种访问模式详情参见存储管理概述,点击确定后在确认配置弹窗中输入 storageClassName 的值,即存储类的名称。确认配置无误后点击确定。
d. 创建 PVC 后,在持久卷声明列表 > 持久卷列可以看见相应的 PV 自动创建,PVC 状态列显示为 Bound,即 PVC 已经与新创建的 PV 绑定。
- 创建应用并挂载 PVC,在 Pod spec 内指定相应的 PVC 名称,且 Pod 和 PVC 需要在同一个 namespace 下。Pod 创建后,可以读写容器内的 /cds-volume 路径来访问相应的 CDS 存储上的内容。
静态挂载块存储
方式一:通过 kubectl 命令行操作
1. 创建持久卷 PV
1apiVersion: v1
2kind: PersistentVolume
3metadata:
4 name: pv-cds
5 namespace: "default"
6spec:
7 accessModes:
8 - ReadWriteOnce
9 capacity:
10 storage: 5Gi
11 csi:
12 driver: "csi-cdsplugin"
13 volumeHandle: "v-xxxx" # 指定挂载的磁盘,格式为磁盘ID
14 fsType: "ext4"
15 nodeAffinity:
16 required:
17 nodeSelectorTerms:
18 - matchExpressions:
19 - key: failure-domain.beta.kubernetes.io/zone
20 operator: In
21 values:
22 - zoneA
23 persistentVolumeReclaimPolicy: Retain说明:
- fsType 不填写时默认值为 ext4。Filesystem 模式下,若 fsType 与 cds 中实际文件系统类型不匹配,将导致挂载失败;若 cds 中尚无文件系统,则挂载时自动格式化 cds 为 fsType 指定的文件系统。
- nodeAffinity 中需要指定 cds 所在可用区,保证挂载该 cds 的 pod 只会被调度到与 cds 磁盘同可用区的 node 上。
2. 创建持久卷声明 PVC
1apiVersion: v1
2kind: PersistentVolumeClaim
3metadata:
4 name: csi-cds-pvc
5spec:
6 accessModes:
7 - ReadWriteOnce
8 resources:
9 requests:
10 storage: 5Gi3. 检查 PVC 状态为 Bound,并且与对应的 PV 绑定
1$ kubectl get pv
2NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
3pv-cds 5Gi RWO Retain Bound default/csi-cds-pvc 4s
4$ kubectl get pvc
5NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
6csi-cds-pvc Bound pv-cds 5Gi RWO 36s4. 在 Pod 中挂载 PVC
1apiVersion: apps/v1
2kind: Deployment
3metadata:
4 name: web-server-deployment
5 labels:
6 test: ws
7spec:
8 replicas: 1
9 selector:
10 matchLabels:
11 se: ws
12 template:
13 metadata:
14 labels:
15 se: ws
16 name: web-server
17 spec:
18 containers:
19 - name: web-server
20 image: nginx
21 volumeMounts:
22 - mountPath: /var/lib/www/html
23 name: csi-cds-pvc
24 volumes:
25 - name: csi-cds-pvc
26 persistentVolumeClaim:
27 claimName: csi-cds-pvcPod 创建后,可以读写容器内的 /var/lib/www/html 路径来访问相应的 CDS 存储上的内容。
由于创建 PV 和 PVC 时只支持 accessModes 为 ReadWriteOnce,该 PVC 可以被同一节点上所有 Pod 挂载读写。
方式二:通过控制台操作
- 登陆 CCE 控制台,单击集群名称进入集群详情页。
- 创建持久卷 PV。
a. 在左侧导航栏选择存储配置 > 持久卷,进入持久卷列表。
b. 点击持久卷列表上方新建持久卷按钮,选择表单创建或 Yaml 创建。
c. 若选择表单创建则需填写相关参数,根据需求设置存储容量,存储类型选择云盘 CDS,并输入云盘 ID。点击确定在二次弹窗中确认配置后点击确定创建 PV。云盘 ID 可前往 CDS 控制台 查看。
- 创建可以和持久卷 PV 绑定的持久卷声明 PVC。
a. 在左侧导航栏选择存储配置 > 持久卷声明,进入持久卷声明列表。
b. 点击持久卷列表上方新建持久卷声明按钮,选择表单创建或 Yaml 创建。
c. 根据之前创建的 PV 配置 PVC 的存储容量、访问模式、存储类(可选),点击确定创建 PVC。会查找现有的 PV 资源,寻找与 PVC 请求相匹配的 PV。
d. 绑定后,可以分别在持久卷列表和持久卷声明列表中看见 PV 和 PVC 的状态列变为 Bound。
- 创建应用并挂载 PVC,在 Pod spec 内指定相应的 PVC 名称即可。
应用场景
在 StatefuleSet 里通过 claimTemple 批量使用 PVC
- 创建 2 副本 StatefuleSet 并指定 volumeClaimTemplates,需要提前创建好相应 StorageClass:
1apiVersion: apps/v1
2kind: StatefulSet
3metadata:
4 name: web
5spec:
6 serviceName: "nginx"
7 replicas: 2
8 selector:
9 matchLabels:
10 app: nginx
11 template:
12 metadata:
13 labels:
14 app: nginx
15 spec:
16 containers:
17 - name: nginx
18 image: nginx
19 ports:
20 - containerPort: 80
21 name: web
22 volumeMounts:
23 - name: www
24 mountPath: /usr/share/nginx/html
25 volumeClaimTemplates:
26 - metadata:
27 name: www
28 spec:
29 accessModes: [ "ReadWriteOnce" ]
30 resources:
31 requests:
32 storage: 5Gi
33 storageClassName: hp1- 查看 Pod 以及自动创建的 PVC。
1$ kubectl get pod
2NAME READY STATUS RESTARTS AGE
3web-0 1/1 Running 0 3m
4web-1 1/1 Running 0 2m1$ kubectl get pvc
2NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
3www-web-0 Bound pvc-a1e885701d2f11e9 5Gi RWO hp1 6m
4www-web-1 Bound pvc-c91edb891d2f11e9 5Gi RWO hp1 5m多可用区集群挂载 CDS
目前 CDS 不支持跨可用区,如果 CCE 集群中有多个可用区的机器,动态挂载的方式可以通过设置 StorageClass 的 Volume Binding Mode 为 WaitForFirstConsumer 来自动根据 Pod 被调度节点所处的可用区创建 CDS 磁盘,或者通过设置 StorageClass 中 allowedTopologies 字段或 Pod 的节点亲和属性来指定可用区;使用已有 CDS 时,须指定 PV 的 nodeAffinity 参数实现可用区亲和性。
CCE 集群默认会为集群节点打上可用区标签:
1$ kubectl get nodes --show-labels
2NAME STATUS ROLES AGE VERSION LABELS
3192.168.80.15 Ready <none> 13d v1.8.12 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/instance-type=BCC,beta.kubernetes.io/os=linux,failure-domain.beta.kubernetes.io/region=bj,failure-domain.beta.kubernetes.io/zone=zoneC,kubernetes.io/hostname=192.168.80.15其中 failure-domain.beta.kubernetes.io/zone=zoneC 标签说明该集群节点处于 C 可用区。
方式一:设置 StorageClass 的 Volume Binding Mode
通过指定 volumeBindingMode 为 WaitForFirstConsumer 来解决此问题。指定绑定模式为 WaitForFirstConsumer 时,先进行 Pod 的调度,随后根据调度结果对应的可用区创建 CDS。
使用示例
- 创建 StorageClass 指定
volumeBindingMode为WaitForFirstConsumer。
1apiVersion: storage.k8s.io/v1
2kind: StorageClass
3metadata:
4 name: csi-cds
5provisioner: csi-cdsplugin
6allowVolumeExpansion: true
7volumeBindingMode: WaitForFirstConsumer
8parameters:
9 paymentTiming: "Postpaid"
10 storageType: "hp1"
11reclaimPolicy: Delete- 在 StatefulSet 中通过 claimTemple 使用 PVC:
1apiVersion: apps/v1
2kind: StatefulSet
3metadata:
4 name: web
5spec:
6 serviceName: "nginx"
7 replicas: 1
8 selector:
9 matchLabels:
10 app: nginx
11 template:
12 metadata:
13 labels:
14 app: nginx
15 spec:
16 containers:
17 - name: nginx
18 image: nginx
19 ports:
20 - containerPort: 80
21 name: web
22 volumeMounts:
23 - name: www
24 mountPath: /usr/share/nginx/html
25 volumeClaimTemplates:
26 - metadata:
27 name: www
28 spec:
29 accessModes: [ "ReadWriteOnce" ]
30 resources:
31 requests:
32 storage: 5Gi
33 storageClassName: csi-cds方式二:通过 StorageClass 的 allowedTopologies 字段强制指定 zone
- 创建 StorageClass 并配置
allowedTopologies为 参数。
1apiVersion: storage.k8s.io/v1
2kind: StorageClass
3metadata:
4 name: hp1-zonec
5provisioner: csi-cdsplugin
6parameters:
7 paymentTiming: "Postpaid"
8 storageType: "hp1"
9reclaimPolicy: Delete
10volumeBindingMode: WaitForFirstConsumer
11allowedTopologies:
12- matchLabelExpressions:
13 - key: failure-domain.beta.kubernetes.io/zone
14 values:
15 - zoneC- 在 StatefulSet 中通过 claimTemple 使用 PVC:
1apiVersion: apps/v1
2kind: StatefulSet
3metadata:
4 name: sts-multi-zone
5spec:
6 serviceName: "nginx"
7 replicas: 1
8 selector:
9 matchLabels:
10 app: nginx
11 template:
12 metadata:
13 labels:
14 app: nginx
15 spec:
16 containers:
17 - name: nginx
18 image: nginx
19 ports:
20 - containerPort: 80
21 name: web
22 volumeMounts:
23 - name: www
24 mountPath: /usr/share/nginx/html
25 volumeClaimTemplates:
26 - metadata:
27 name: www
28 spec:
29 accessModes: [ "ReadWriteOnce" ]
30 resources:
31 requests:
32 storage: 40Gi
33 storageClassName: hp1-zonec扩容 CDS PV
扩容 CDS PV 需要集群 Kubernetes 版本为 1.16 及以上,同时只针对动态创建的 CDS PV 生效。
- 创建 storageClass 并添加
allowVolumeExpansion: true配置
1apiVersion: storage.k8s.io/v1
2kind: StorageClass
3metadata:
4 name: hp1
5allowVolumeExpansion: true #允许磁盘扩容
6...- 修改与 PV 绑定的 PVC 中
spec.resources.requests中的磁盘容量为目标容量,触发扩容
1kind: PersistentVolumeClaim
2apiVersion: v1
3metadata:
4 name: csi-pvc-cds
5spec:
6 accessModes:
7 - ReadWriteOnce
8 storageClassName: hp1
9 resources:
10 requests:
11 storage: 8Gi #修改为目标磁盘大小-
默认情况下 CDS CSI 插件仅支持离线扩容,即需要在 PVC 未被 Pod 挂载时才会执行实际扩容动作。完成 PVC 容量 request 修改后,如果此时该 PVC 未被任何 Pod 挂载,则会触发 CDS 磁盘扩容操作,否则会等待挂载该 PVC 的 Pod 停止后才开始扩容。具体扩容进度可以通过
kubectl describe pvc <pvcName>查看对应的 Events 了解。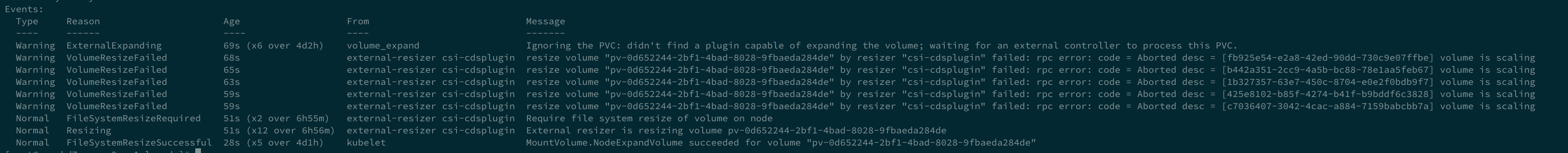
说明:
- 如果需要在 PVC 被 Pod 挂载状态下进行在线扩容,可以通过
kubectl -n kube-system edit deployment csi-cdsplugin-controller-server,给csi-cdsplugin容器的添加启动参数--enable-online-expansion`,来启用在线扩容功能。- 但需要特别注意的是,高负载情况下在线扩容可能会出现IO性能下降或导致IO错误,建议选择低负载时操作并提前创建快照备份。
