通过YAML创建CCE_Ingress
本文档介绍如何通过YAML创建和管理CCE Ingress。
本文档主要包含以下内容:
1.部署CCE Ingress Controller
2.创建Deployment与Service
3.创建CCE Ingress
注意:一个CCE Ingress只能使用一个BLB,一个BLB也只能被一个CCE Ingress使用
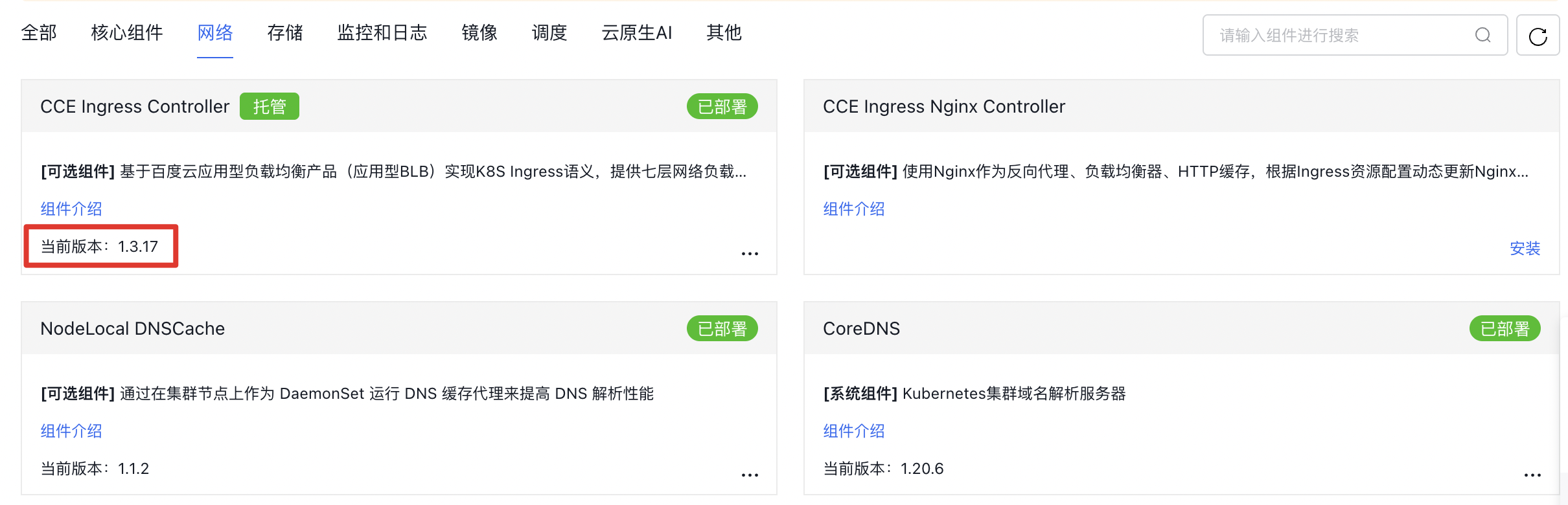
部署CCE Ingress Controller
CCE Ingress使用百度智能云负载均衡产品(BLB)实现,亦称为BLB类型Ingress。
CCE Ingress的使用需要集群中部署CCE Ingress Controller组件。
CCE不会为集群默认安装Ingress Controller,用户可在组件管理中安装该组件。
- 进入集群控制台“组件管理>网络”,找到
CCE Ingress Controller组件。
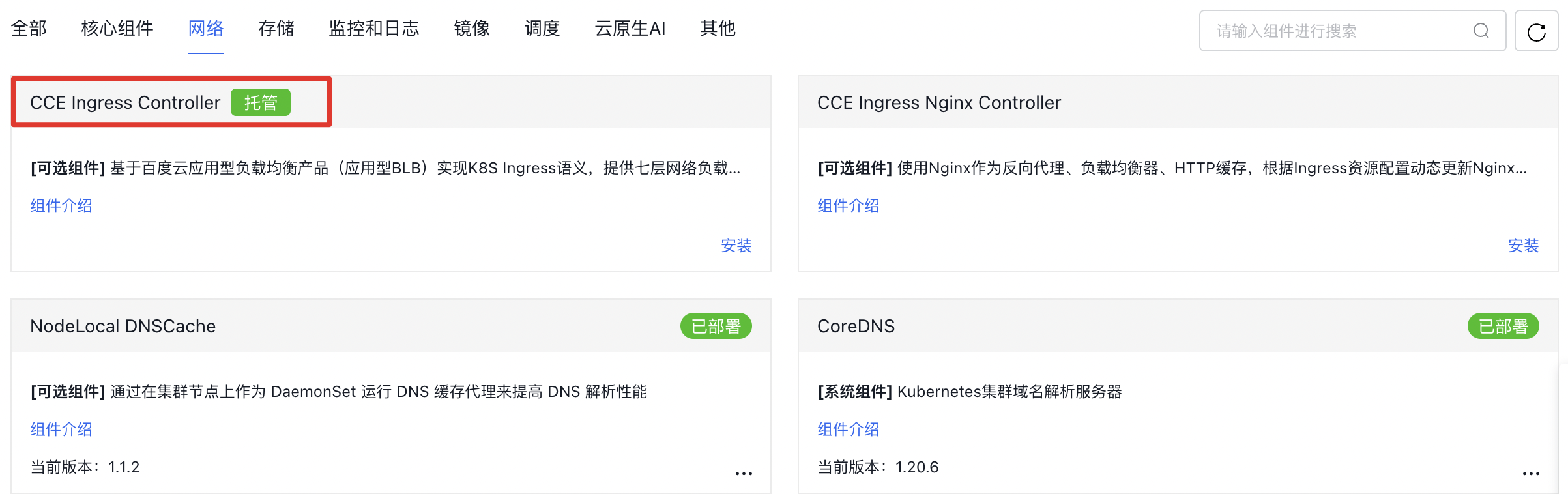
- 点击『安装』并确认。
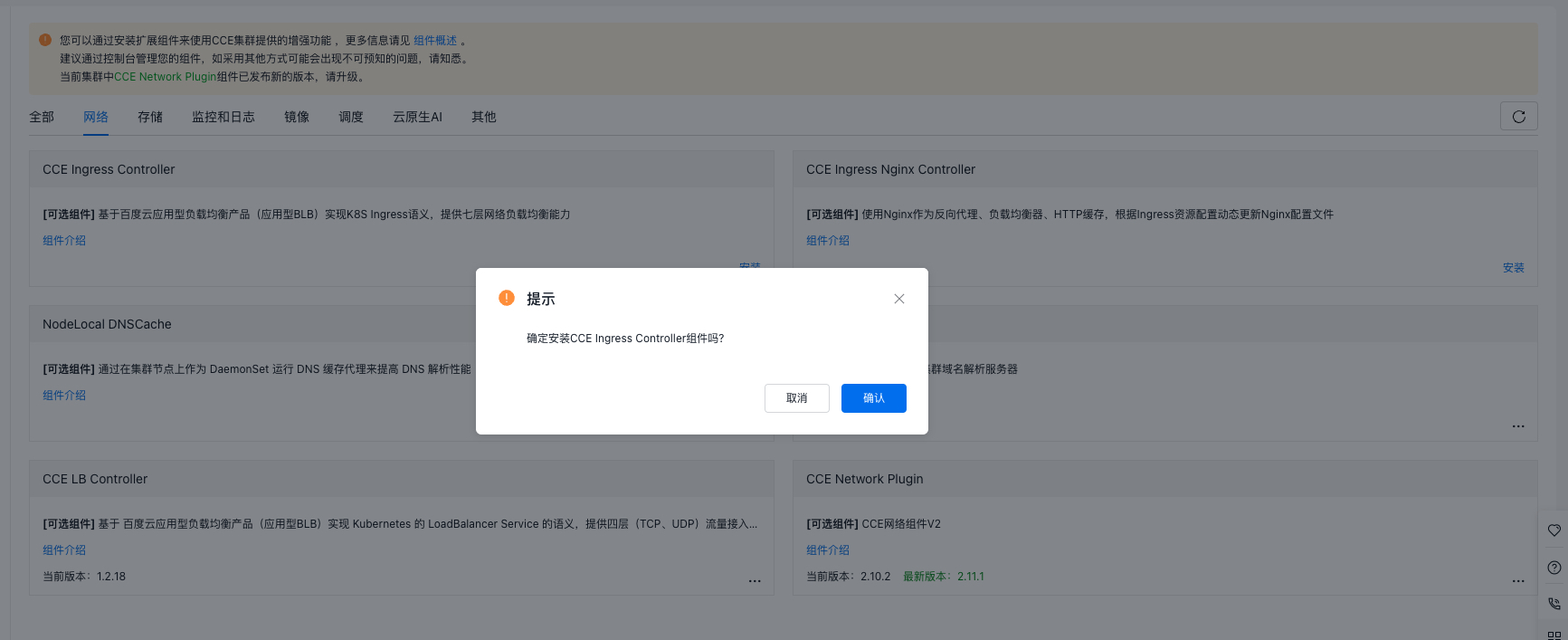
- 等待
CCE Ingress Controller组件显示 "当前版本",表示该组件安装成功。
创建示例Deployment和Service
1apiVersion: apps/v1
2kind: Deployment
3metadata:
4 name: ingress-nginx-deployment
5 labels:
6 app: ingress-nginx
7spec:
8 replicas: 2
9 selector:
10 matchLabels:
11 app: ingress-nginx
12 template:
13 metadata:
14 labels:
15 app: ingress-nginx
16 spec:
17 containers:
18 - name: nginx
19 image: hub.baidubce.com/cce/nginx-ingress
20 ports:
21 - containerPort: 80
22---
23kind: Service
24apiVersion: v1
25metadata:
26 name: hello-service
27spec:
28 selector:
29 app: ingress-nginx
30 type: NodePort
31 ports:
32 - protocol: TCP
33 port: 8000
34 targetPort: 80
35---
36kind: Service
37apiVersion: v1
38metadata:
39 name: world-service
40spec:
41 selector:
42 app: ingress-nginx
43 type: NodePort
44 ports:
45 - protocol: TCP
46 port: 9000
47 targetPort: 80创建Ingress对象
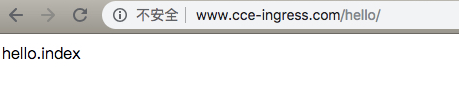
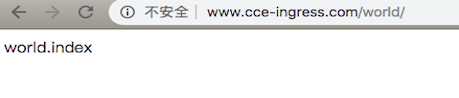
使用以下yaml内容创建名为helloworld的Ingress对象,并配置Ingress转发规则:
- www.cce-ingress.com/hello/ -> hello-service:8000/hello/
- www.cce-ingress.com/world/ -> world-service:9000/world/
可通过Ingress Annotations中的参数对Ingress进行配置,例如指定BLB或EIP。
Service对应后端服务必须支持转发策略的URI,如果要支持所有情况,建议设置为/*,这里对URI的路径要求很严格注意“/”。
1apiVersion: networking.k8s.io/v1
2kind: Ingress
3metadata:
4 annotations:
5 cce.ingress.blb-backup-content: ""
6 kubernetes.io/cce.ingress.blb-cert-id: ""
7 kubernetes.io/cce.ingress.blb-id: ""
8 kubernetes.io/cce.ingress.eip: ""
9 kubernetes.io/cce.ingress.http-redirect: "false"
10 kubernetes.io/cce.ingress.https: "false"
11 kubernetes.io/cce.ingress.internal: "false"
12 kubernetes.io/cce.ingress.timeout-in-seconds: "30"
13 kubernetes.io/cce.ingress.vpc-subnet-id: ""
14 kubernetes.io/ingress.class: cce
15 name: helloworld
16 namespace: default
17spec:
18 rules:
19 - host: www.cce-ingress.com
20 http:
21 paths:
22 - backend:
23 service:
24 name: hello-service
25 port:
26 number: 8000
27 path: /hello/*
28 - backend:
29 service:
30 name: world-service
31 port:
32 number: 9000
33 path: /world/*下文描述了创建CCE Ingress时,需要注意的事项。
Ingress Class
CCE Ingress Controller仅处理带有kubernetes.io/ingress.class: cce注释的Ingress,请确保Ingress带有该Annnotation。
HTTPS规则设置
CCE Ingress Controller默认将Ingress资源的规则创建为HTTP规则,不会为其配置HTTPS规则,如果要将某些规则配置为HTTPS规则,应该具有以下Annotation:
-
指定BLB使用的证书。
Plain Text1kubernetes.io/cce.ingress.blb-cert-id: cert-id -
显式声明开启HTTPS。
Plain Text1kubernetes.io/cce.ingress.https: "true" -
指明使用HTTPS的规则。如果Spec中的某些规则需要使用HTTPS,还需要添加到该Annotation中。
Plain Text1kubernetes.io/cce.ingress.https-rules: >- 2 [ 3 { "host":"ad.com", 4 "http":{ 5 "paths":[ 6 {"path":"/*","backend":{"serviceName":"service-example","servicePort":80}} 7 ] 8 } 9 } 10 ]
完整的Annotation使用说明参考:BLB Ingress Annotation说明。
访问测试
修改本地/etc/hosts,将www.cce-ingress.com指向EIP(例如: 106.12.52.80),可在控制台或者集群内查看Ingress信息:
1# kubectl get ingress
2NAME HOSTS ADDRESS PORTS AGE
3helloworld www.cce-ingress.com 10.0.3.251,106.12.52.80 80 6m34s访问测试: